RC4原理和实现
RC4
¶基本原理
RC4属于对称密码算法中的流密码加密算法
密钥长度可变,面向字节操作
以一个足够大的S表为基础,对表进行非线性变换,产生密钥流
两次交换过程是为了增加随机性
¶加密过程
¶初始化S表
1、对S表进行先行填充,一般为256字节,且为unsigned类型
2、用种子密钥填充另一个256字节的K表
如果种子密钥长度不为256,将循环使用种子密钥对K表进行填充
3、用 K表对S表进行初始置换
¶样例展示
这里我们假设S表和K表都是7个字节的,密钥为345,填充结果如下
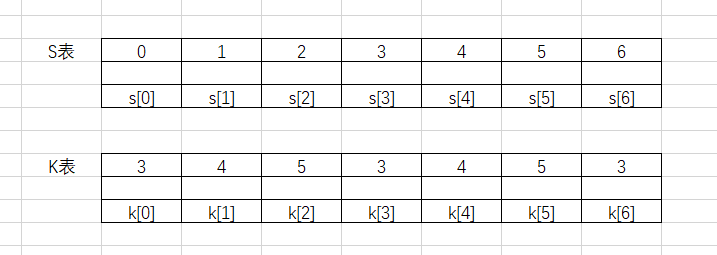
使用K表对S表进行置换
1 | int j = 0; |
得到被置换后的S表
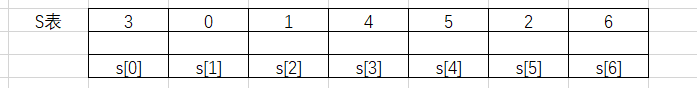
¶生成密钥流
作用:为每个待价密的字节生成一个伪随机数,用来异或
注:S表完成初始化之后,种子密钥将不会再被使用
使用置换后的S表生成密钥流
1 | int i, j = 0; |
¶加密过程
密钥流和明文进行异或得到密文
¶最终代码
加密部分的j是用来打乱的,实现伪随机
1 |
|
可以不保存密钥流,直接进行异或,逆向的时候我们可以动调得到密钥流,再与密文进行异或就可以得到明文了
1 | void Rc4_encrypt(unsigned char* S, unsigned char* flag,char*flag1) |
分别看一下加密过程的逆向代码
直接异或,动调根据存储的寄存器进行提取
1 | __int64 __fastcall Rc4_encrypt(unsigned __int8 *a1, unsigned __int8 *a2, char *a3) |
先保存再异或
1 | __int64 __fastcall Rc4_encrypt(unsigned __int8 *a1, unsigned __int8 *a2, signed int a3) |
可以看到密钥流存储在v9,动调之后可以直接提取
Vs2022生成的exe文件反编译
1 | __int64 __fastcall sub_140015E30(__int64 a1, __int64 a2, char *a3) |
看着跟别的不一样
¶题目——BUU-[GUET-CTF2019]encrypt
拖进ida,对一些变量和函数名进行识别和改名
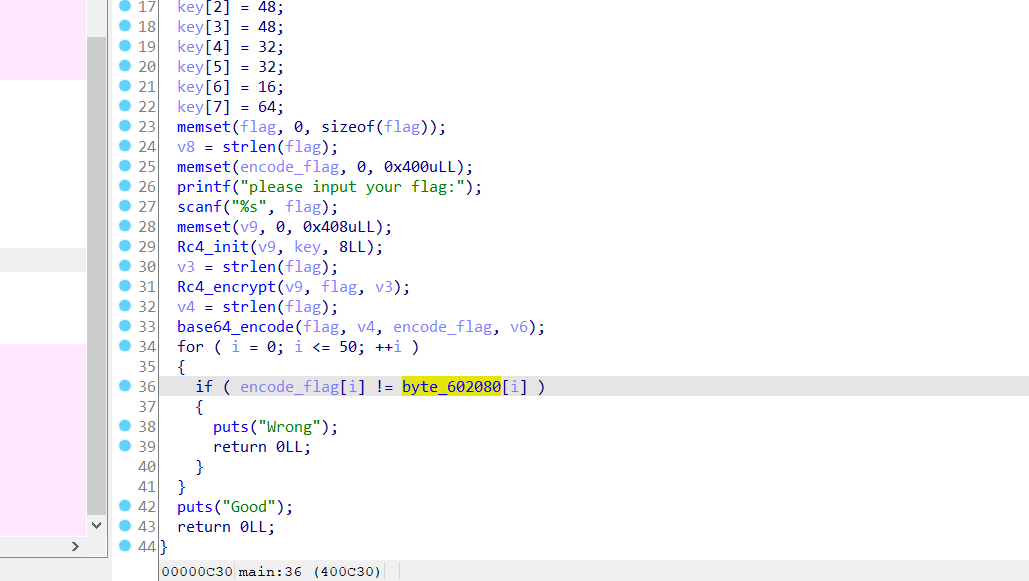
点进加密函数进行查看

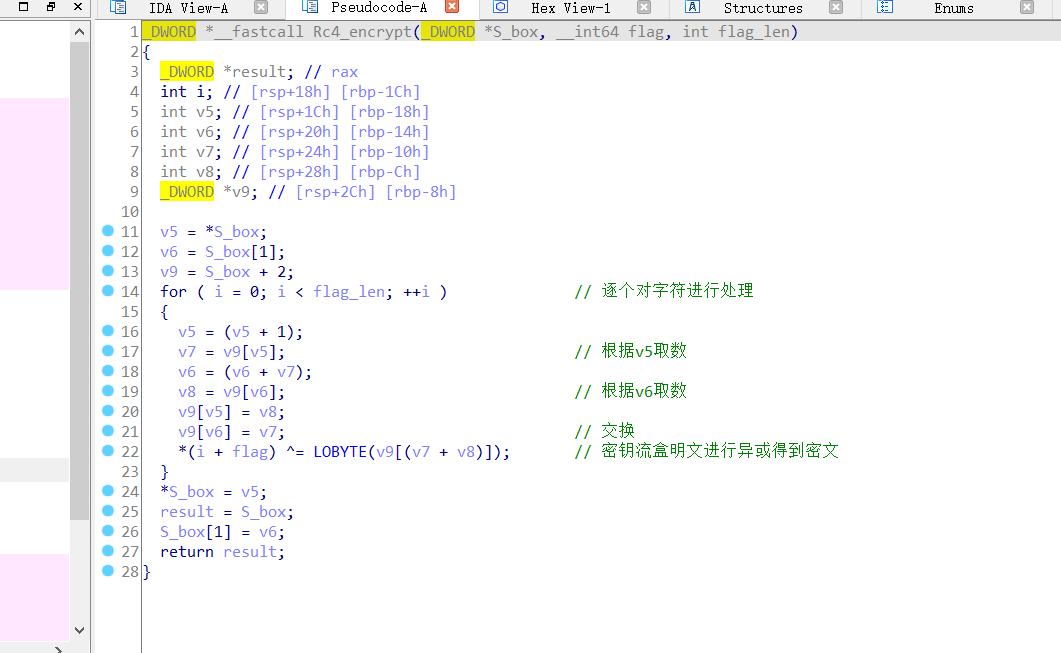
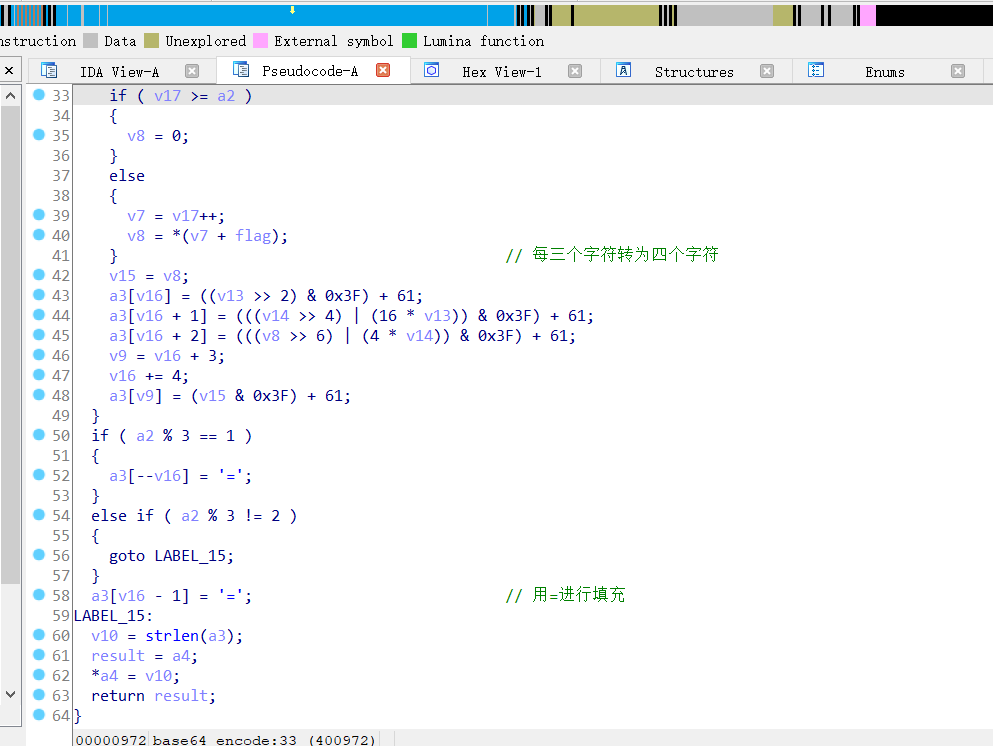
整体就是先RC4,然后将加密后的三个字符变为四个字符
逆向过来先将四个字符转为三个字符,然后直接将转换后的结果和密钥流进行异或得到明文
密钥流可以通过动调得到
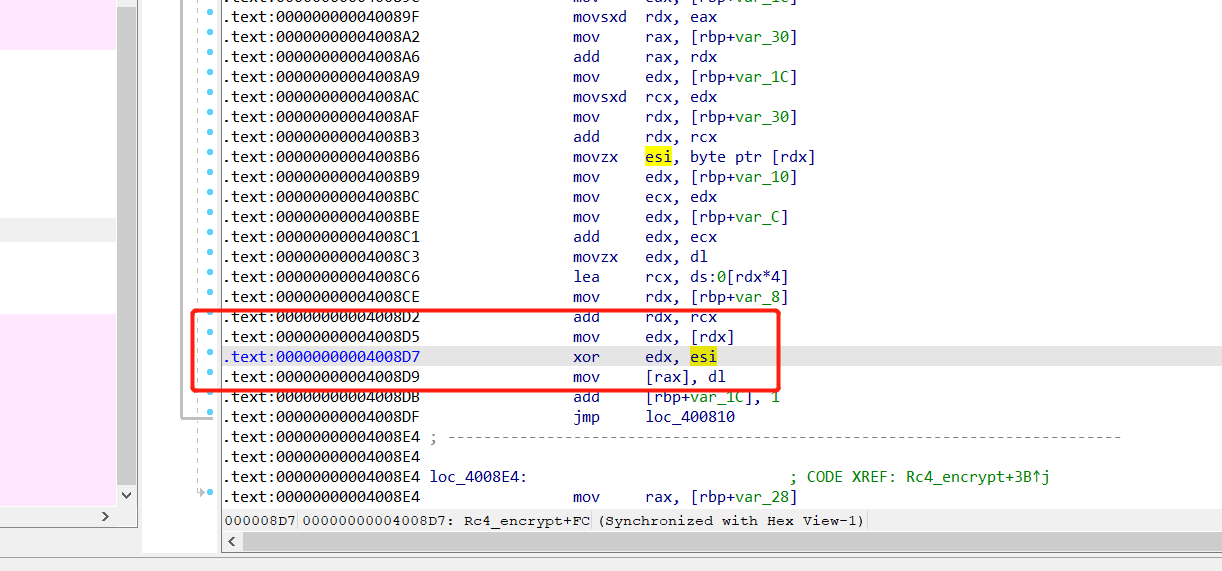
脚本
1 |
|