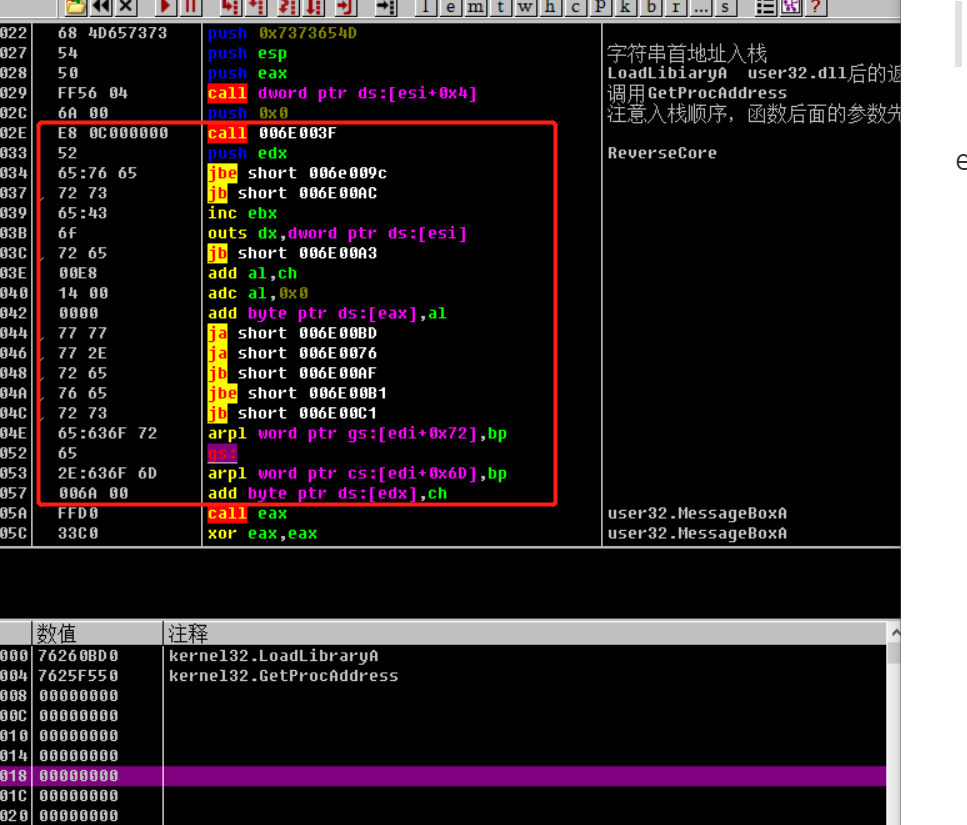
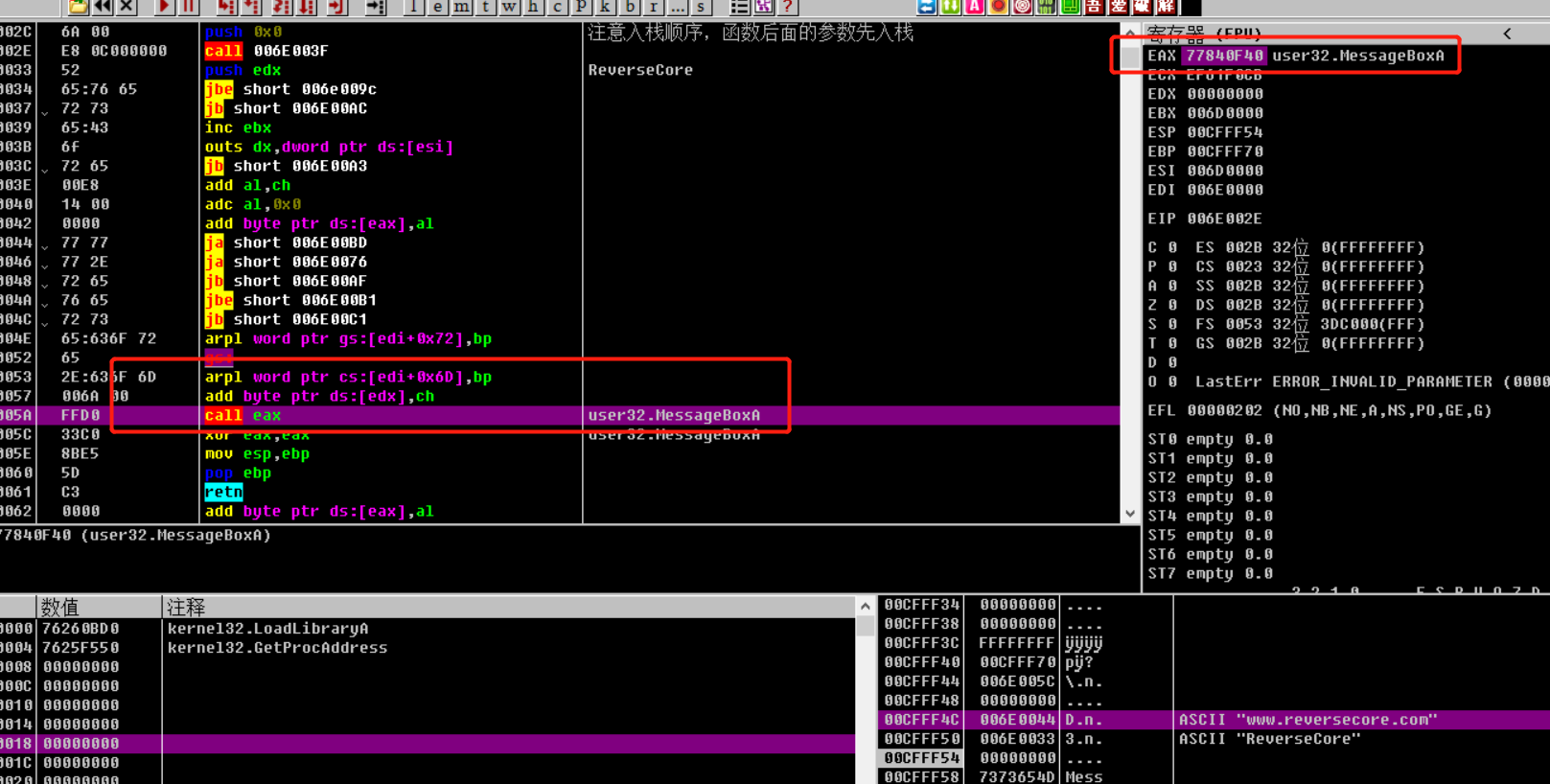
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
48
49
50
51
52
53
54
55
56
57
58
59
60
61
62
63
64
65
66
67
68
69
70
71
72
73
74
75
76
77
78
79
| #include<stdio.h>
#include<Windows.h>
#include<string.h>
BYTE shellcode[] = {
0x55,0x8B,0xEC,0x8B,0x75,0x08,0x68,0x6C,0x6C,0x00,0x00,0x68,0x33,0x32,0x2E,0x64
,0x68,0x75,0x73,0x65,0x72,0x54,0xFF,0x16,0x68,0x6F,0x78,0x41,0x00,0x68,0x61,0x67
,0x65,0x42,0x68,0x4D,0x65,0x73,0x73,0x54,0x50,0xFF,0x56,0x04,0x6A,0x00,0xE8,0x0C
,0x00,0x00,0x00,0x52,0x65,0x76,0x65,0x72,0x73,0x65,0x43,0x6F,0x72,0x65,0x00,0xE8
,0x14,0x00,0x00,0x00,0x77,0x77,0x77,0x2E,0x72,0x65,0x76,0x65,0x72,0x73,0x65,0x63
,0x6F,0x72,0x65,0x2E,0x63,0x6F,0x6D,0x00,0x6A,0x00,0xFF,0xD0,0x33,0xC0,0x8B,0xE5
,0x5D,0xC3
};
typedef struct _Thread_Param
{
FARPROC pFunc[2];
}Thread_Param, * pThread_Param;
void Asm_Inject(DWORD PID)
{
HMODULE hMod = NULL;
HANDLE hProcess = NULL;
Thread_Param param[2] = { 0, };
HANDLE hThread = NULL;
LPVOID pRemoteBuf[2] = { 0, };
hMod = GetModuleHandleA("kernel32.dll");
param->pFunc[0] = GetProcAddress(hMod, "LoadLibraryA");
param->pFunc[1] = GetProcAddress(hMod, "GetProcAddress");
if (!(hProcess = OpenProcess(PROCESS_ALL_ACCESS, FALSE, PID)))
{
printf("Open Failed!!Error Code:%d\n", GetLastError());
return;
}
if (!(pRemoteBuf[0] = VirtualAllocEx(hProcess, NULL, sizeof(Thread_Param), MEM_COMMIT, PAGE_READWRITE)))
{
printf("VirtualAlloc Failed!!Error Code:%d\n", GetLastError());
return;
}
if (!WriteProcessMemory(hProcess, pRemoteBuf[0], (LPVOID)¶m, sizeof(Thread_Param), NULL))
{
printf("WriteProcess Failed!!Error Code:%d\n", GetLastError());
return;
}
if (!(pRemoteBuf[1] = VirtualAllocEx(hProcess, NULL, sizeof(shellcode), MEM_COMMIT, PAGE_READWRITE)))
{
printf("VirtualAlloc Failed!!Error Code:%d\n", GetLastError());
return;
}
if (!WriteProcessMemory(hProcess, pRemoteBuf[1], (LPVOID)&shellcode, sizeof(shellcode), NULL))
{
printf("WriteProcess Failed!!Error Code:%d\n", GetLastError());
return;
}
hThread = CreateRemoteThread(hProcess, NULL, 0, (LPTHREAD_START_ROUTINE)pRemoteBuf[1], pRemoteBuf[0], 0, NULL);
WaitForSingleObject(hThread, INFINITE);
CloseHandle(hThread);
CloseHandle(hProcess);
return;
}
int main(int argc,char*argv[])
{
Asm_Inject((DWORD)atol(argv[1]));
return 0;
}
|